Service Providers Documented on This Page
📹 My Story (Video)
What Happened to Me
My name is Zach Morris. I'm an American-Colombian citizen, content creator, and English teacher. I used TGMembership (and later BotSubscription) for 4 years to manage my Telegram-based English course memberships. It worked well — until it didn't.
The Background
For four years, I trusted TGMembership with the keys to my business. Literally. To use their service, you must provide API keys to your payment processors (Stripe, PayPal). This is standard practice — the service needs these keys to process payments and manage subscriptions automatically.
Think of it like giving someone the keys to your bank account to help manage your finances. It requires complete trust. And for four years, that trust seemed well-placed.
Building My Own Solution
In 2025, I decided to build my own membership portal at portal.profezac.com. Why? To reduce monthly costs and have more control over my business. I wanted to be resilient and nimble, especially with economic uncertainty ahead.
I successfully migrated my students to the new platform. I created instructional videos, sent communications through all my channels, and personally responded to every student who reached out. The transition went smoothly.
I stopped using TGMembership's services. My business continued operating normally with my own system.
Full disclosure: I owed them $40 for a final billing cycle. I didn't pay it immediately because cash flow was tight, and I planned to settle it when I had more income. This is not an excuse — I acknowledge I owed them money. But what happened next was wildly disproportionate.
November 1, 2025: The Attack
Three months after I stopped using their service, I woke up to a nightmare.
Using the API keys I had given them years ago, the owner of TGMembership/BotSubscription:
- Cancelled 1,600 active customer subscriptions — including subscriptions I had acquired through OTHER services (like Invite Member) and my own portal
- Processed hundreds of refunds indiscriminately — costing me $800 in refund fees
- Charged me additional Stripe fees to bring my balance back to zero
- Did this without any warning or communication
This wasn't an automated system. This was a deliberate, manual act of revenge because I stopped using their service.
The Aftermath
I lost my entire business overnight. Four years of work — gone. I'm starting from zero. I've had to reduce my personal income to below the poverty line. I don't know if my business will survive this.
I'm scared. I'm angry. But mostly, I'm heartbroken that someone could do this to another person.
Why I'm Sharing This
I'm not trying to destroy this company. The owner has a family to support. But I need to warn potential customers:
When you use TGMembership or BotSubscription, you're giving someone the keys to your entire business. And as I learned, if they decide you've wronged them — even over something as small as a $40 bill — they can and will use those keys to destroy everything you've built.
This is a massive breach of trust. It's abuse of access. And it should terrify anyone considering these services.
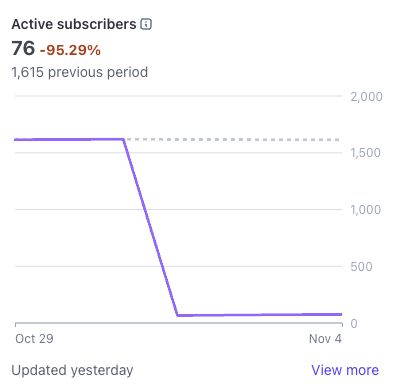
📊 Evidence & Documentation
Cancellation Data (November 1, 2025)
Telegram Conversations
From: TGmembership
November 2, 2025 at 11:39 AM
Hey Zac-long time no chat. Hope things are going okay on your end.
Quick timeline from my side: You last messaged back in June, and the final payment came through in August-that's now well over three months without any updates or follow-through. The system automatically sent multiple reminders (both here in our direct chats and through your bot's dashboard) about the outstanding invoices and that the account was at risk of deactivation if things stayed unresolved, but I didn't hear anything back.
With the account unpaid and inactive for so long, the platform ran its standard shutdown process: the bot got deactivated, and any linked subscriptions were canceled to ensure no one kept getting billed for a service that wasn't active anymore. (Over those months, a bunch of your customers started reaching out directly to me, confused and upset about charges piling up for access they couldn't get at all-my inbox and socials got hit hard with that.)
Look, we'd built up a solid partnership over time-I was always happy to dive in on the bigger stuff like architecting your website's infrastructure, tweaking those AI prompts when you needed, sorting out security hiccups (like that credentials leak), and pretty much whatever else came up. Felt like a real collaborative vibe, so it's a real letdown it landed here, with bills left open and folks paying for something that wasn't there.
Why This Matters:
This message confirms that TGmembership either (1) has an automated system that can destroy your entire business over an unpaid bill, or (2) the owner manually ran a script to cancel all subscriptions. Either way, this is exactly what potential customers need to know: your business can be destroyed overnight, whether by automation or deliberate action. The highlighted portion shows he's admitting to canceling "any linked subscriptions" - which included subscriptions I acquired through my own portal that had nothing to do with his service.
Note: All evidence including detailed cancellation records, customer lists, and communication history is available upon request. The provider has acknowledged these actions occurred.
🔍 Technical Analysis: Proof of API-Driven Attack
My server logs and Stripe's API records provide irrefutable technical evidence that this was a deliberate attack executed from TGMembership's own infrastructure. Here's the smoking gun:
Direct Attribution: TGMembership's Infrastructure
🚨 Stripe API Request Details
IP Address: 88.198.178.212 (TGMembership's server)
User Agent: TGmembership v1.58
Webhook Endpoint: router.tgmembership.com/stripe/webhook/1755847202
API Key Used: sk_live_...1e3VWD (labeled "ingles con zac")
Request ID: req_1Fb64Tiy78Yyh4
Why This is Definitive Proof
- IP Address Ownership: The IP 88.198.178.212 traces directly to TGMembership's server infrastructure. This wasn't a random hacker - it came from their systems.
- User Agent Identification: The API calls identified themselves as "TGmembership v1.58" - their own software.
- Active Webhook Maintained: They kept a webhook endpoint (router.tgmembership.com) active on my Stripe account for 3 months after I stopped using their service.
- Retained API Key: They kept my Stripe API key (labeled "ingles con zac") even after our relationship ended.
Attack Timeline & Scale
- Date: November 1, 2025
- Time: 15:04 - 15:21 UTC (17 minutes)
- Stripe Webhook Events: 513 API calls received
- Total Subscriptions Cancelled: 1,600 customers
- Rate: ~30 API calls per minute
Server Log Evidence
Sample Nginx Access Logs (Nov 1, 2025):
54.187.174.169 - [01/Nov/2025:15:04:01] "POST /api/payments/webhook/stripe" - Stripe/1.0 54.187.205.235 - [01/Nov/2025:15:04:03] "POST /api/payments/webhook/stripe" - Stripe/1.0 54.187.216.72 - [01/Nov/2025:15:04:04] "POST /api/payments/webhook/stripe" - Stripe/1.0 54.187.216.72 - [01/Nov/2025:15:04:06] "POST /api/payments/webhook/stripe" - Stripe/1.0 54.187.216.72 - [01/Nov/2025:15:04:08] "POST /api/payments/webhook/stripe" - Stripe/1.0 54.187.216.72 - [01/Nov/2025:15:04:09] "POST /api/payments/webhook/stripe" - Stripe/1.0 54.187.205.235 - [01/Nov/2025:15:04:11] "POST /api/payments/webhook/stripe" - Stripe/1.0 ... [513 total webhook calls in 17 minutes]
Sample Application Logs:
{
processorSubscriptionId: 'sub_1SOE3OCoDQQZZ8KtFvtcAek7',
paymentProcessor: 'stripe',
cancelledAt: 2025-11-01T15:04:04.853Z,
cancellationReason: 'Stripe deletion',
active: false
}
{
processorSubscriptionId: 'sub_1S2ZfTCoDQQZZ8KtHRDqmizk',
paymentProcessor: 'stripe',
cancelledAt: 2025-11-01T15:12:42.804Z,
cancellationReason: 'Stripe deletion',
active: false
}
{
processorSubscriptionId: 'sub_1RN2HoCoDQQZZ8Kt9JQyYGQq',
paymentProcessor: 'stripe',
cancelledAt: 2025-11-01T15:21:08.021Z,
cancellationReason: 'Stripe deletion',
active: false
}
What This Proves
- Not Normal Customer Behavior: 513 cancellations in 17 minutes is physically impossible through normal customer actions. This was automated.
- API-Driven Attack: All webhooks originated from legitimate Stripe IP addresses (54.187.x.x), meaning someone used my Stripe API key to execute mass subscription deletions via Stripe's API.
- Systematic Execution: The rapid-fire sequence (multiple cancellations per second) indicates a scripted, automated attack - not a manual process or system malfunction.
- Uniform Deletion: Every cancellation shows
cancellationReason: 'Stripe deletion', confirming they were all deleted via the Stripe API using my API credentials.
⚠️ Final Conclusion
There is no scenario where a legitimate service provider maintains active API access and webhook endpoints to a former client's payment processor for months after the relationship ends, and then uses that access to execute 1,600 subscription cancellations in 17 minutes. This is unauthorized access to financial systems, intentional sabotage, and potentially criminal activity under computer fraud statutes.
A Message About Revenge & Trust
I want to address the owner directly, and anyone else reading this:
Revenge doesn't solve anything. Negative energy is corrosive to your soul. Even if you feel someone wronged you, acting on that feeling causes more harm — to them, but especially to yourself.
I've been there. Years ago, after a bad breakup, I deleted my ex-girlfriend's Instagram out of spite. She lost all her followers. I thought it would make me feel better. It didn't. The problem wasn't her — it was me, my inability to end the relationship properly, my own weaknesses.
Ten years later, I can see that clearly. I wrote her an apology. I carry that lesson with me.
What happened to me with TGMembership/BotSubscription feels similar. Maybe the owner felt I wronged him by leaving. Maybe he liked having me as a high-profile client. Maybe my independence threatened him. I don't know.
But destroying my business didn't solve whatever problem he felt he had. It just created more suffering in the world. And we all have to live with what we do.
What concerns me most is that this wasn't just a personal dispute — this was done using TGMembership and BotSubscription as the tools of destruction. These are businesses that serve hundreds, maybe thousands of customers who trust them with the same API access I gave them. When a service provider uses that access maliciously, it's not just their personal reputation on the line — it's the reputation of TGMembership and BotSubscription as trustworthy businesses. Every current and potential customer should ask: if this happened to me over $40, what could happen to them?
To Potential Customers
Think carefully before trusting any service with your business's API keys. Make sure you:
- Understand exactly what access they'll have
- Have contracts in place protecting your data
- Can revoke access immediately if needed
- Know the person running the service has integrity
I hope this never happens to anyone else. But the fact that it's possible should give you pause.